Principles of Cyber Security
The importance and relevancy of cybersecurity are ever-increasing and can be in every walk of life. News headlines fill our screens, ......
The importance and relevancy of cybersecurity are ever-increasing and can be in every walk of life. News headlines fill our screens, reporting yet another hack or data leak.
What makes a hacker bad?
Right and wrong are relative concepts. We can have hour-long moral debate between right and wrong; where an action may be legal, it may be perceived to be wrong by someone.
Hackers are sorted into three hats, where their ethics and motivations behind their actions determine what hat category they are placed into.
White Hat: These hackers are considered the “good people”. They remain within the law and use their skills to benefit others. For example, a penetration tester performing an authorised engagement on a company.
Grey Hat: These people use their skills to benefit others often; however, they do not respect/follow the law or ethical standards at all times. For example, someone taking down a scamming site.
Black Hat: These people are criminals and often seek to damage organisations or gain some form of financial benefit at the cost of others. For example, ransomware authors infect devices with malicious code and hold data for ransom.
Sounds bad, doesn’t it? But you can take some steps towards minimizing your exposure to such attacks. Mind you, you won’t be hack-proof. But these principles of information security can help you secure data and protect your systems from abuse.
Principles of Information Technology
I’ll list some of the fundamental principles of information security. The frameworks used to protect data and systems to the elements of what exactly makes data secure. The measures, frameworks and protocols discussed, all play a small part in mounting your defence against “bad actors”.
The CIA triad “CIA” the has nothing to do with a certain well-recognized US intelligence agency. It is an information security model that is used in consideration throughout creating a security policy.
Consisting of three sections: Confidentiality, Integrity and Availability (CIA), this model has quickly become an industry standard today. This model should help determine the value of data that it applies to, and in turn, the attention it needs from the business.

The CIA triad is a continuous cycle. Whilst the three elements to the CIA triad can arguably overlap, if even just one element is not met, then the other two are rendered useless.
Whilst the three elements to the CIA triad are arguably self-explanatory, let’s explore these and contextualise them into cybersecurity.
Confidentiality
This element is the protection of data from unauthorized access and misuse. Organisations will always have some form of sensitive data stored on their systems. For example, governments using a sensitivity classification rating system (top-secret, classified, unclassified)
Integrity
In the CIA triad, integrity is maintained when the information remains unchanged during storage, transmission, and usage not involving modification to the information. Access control and Authentication can help prevent authorized users from making unauthorized changes. Hash verifications and digital signatures can help ensure that transactions are authentic and that files have not been modified or corrupted.
Availability
The main concern in the CIA triad is that the information should be available when authorised users need to access it. Availability is very often a key benchmark for an organisation. When a system is unavailable, it often results in damage to an organisations reputation and loss of finances.
Principles of Privileges
It is vital to administrate and correctly define the various levels of access to an information technology system individuals require.
The levels of access given to individuals are determined on two primary factors:
- The individual’s role
- The sensitivity of the information
Privileged Identity Management and Privileged Access Management .
Initially, these two concepts can seem to overlap; however, they are different from one another. PIM is used to translate a user’s role within an organisation Whereas PAM is the management of the privileges a role has, amongst other things. (Just like discord)
Rule of thumb is, users should be given the minimum amount of privileges, and only those that are absolutely necessary for them to perform their duties.
Security Models
Let’s explore some popular and effective security models used to achieve the three elements of the CIA triad.
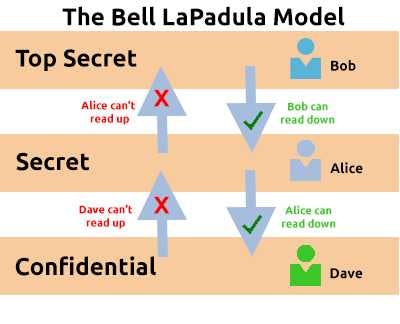
The Bell-La Padula Model
The Bell-La Padula Model is used to achieve confidentiality. This model has a few assumptions, such as an organisation’s hierarchical structure it is used in, where everyone’s responsibilities/roles are well-defined.
The model works by granting access to pieces of data (called objects) on a strictly need to know basis. This model uses the rule “no write down, no read up”. Policies in this model can be replicated to real-life organisations hierarchies. Even though a user may not have access to an object, they will know about its existence — so it’s not confidential in that aspect
Biba Model
The Biba model is arguably the equivalent of the Bell-La Padula model but for the integrity of the CIA triad.
This model applies the rule to objects (data) and subjects (users) that can be summarised as “no write up, no read down”. This rule means that subjects can create or write content to objects at or below their level but can only read. The level of abstraction used in such models can prove detrimental to an organization. For example, A principal wouldn’t be able to read notes/results prepared by teachers.
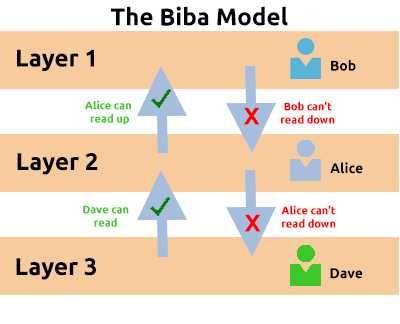
It’s usefulness is where the need for integrity supersedes the need for confidentiality For example, in software development, developers may only have access to the code that is necessary for their job. They may not need access to critical pieces of information.
Threat Modelling
Threat modelling is the process of reviewing, testing and improving security protocols; It includes, identifying likely threats that an application or system may face, the vulnerabilities a system or application may be vulnerable to.
An effective threat model includes:
- Threat intelligence
- Asset identification
- Mitigation capabilities
- Risk assessment
To help with this, there are frameworks such as STRIDE and PASTA.
What should you do after a breach has occured?
A breach of security is known as an incident. Actions taken to resolve and remediate the threat are known as Incident Response (IR)
Incidents are classified using a rating of urgency and impact. Urgency will be determined by the type of attack faced, where the impact will be determined by the affected system and what impact that has on business operations.
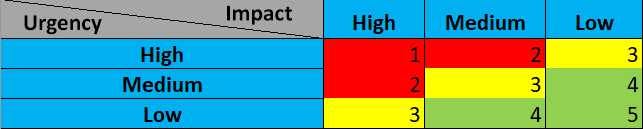
An incident is responded to by a Computer Security Incidentify Response Team (CSIRT) . To successfully solve an incident, these steps are often referred to as the 5 phases of Incident Response that takes place:
- Preparation: Do we have the resources and plans in place to deal with the security incident?
- Identification: Has the threat and the threat actor been correctly identified in order for us to respond to?
- Containment: Can the threat/security incident be contained to prevent other systems or users from being impacted?
- Eradication: Remove the active threat.
- Lessons Learned: What can be learnt from the incident? I.e. if it was due to a phishing email, employees should be trained better to detect phishing emails.
